Cryptology: An Essential Science In Data Security


The Covid-19 pandemic accelerated the digital transformation of companies, but it also led to an unprecedented increase in cybercrime. The media coverage of IT security incidents has a lasting impact on the image of companies in the eyes of the public and their partners, and personal data breaches can have a significant impact on the privacy of the individuals concerned. It is therefore more important than ever to ensure compliance with the applicable regulations on personal data protection and the technical and organizational security of information systems. One of the most important public concerns in terms of data protection is the confidentiality of the information they provide to companies or that they generate by using their services. This is why the most popular messaging solutions (Whatsapp, Telegram, Signal, Facebook Messenger etc.) have been competing in the media over the issue of “ end-to-end encryption” of their users’ messages in recent months. However, the preservation of the confidentiality of messages is an issue that mankind has been facing since 450 BCE, by using cryptology.
Cryptology is the science of secret messages. It has undergone many metamorphoses over the centuries and with the new technologies and uses that have been developed. In order to understand the modern applications of cryptology, it is necessary to detail the essential notions.
Cryptography is the set of techniques and methods used to transform a clear message into an unintelligible message.
Cryptography works through a system of ciphers. It is an encryption system where each letter of the original message is replaced by another (or by a symbol) following a well-defined algorithm. There are two types:
The substitution cipher: each letter is replaced by another but keeps its original place. The substitution cipher can be:
– Monoalphabetic (each character in the original message is always replaced by the same other character).
– Polyalphabetic (the same character in the original message can be replaced by several different characters).
– Polygraphic (characters are not replaced one by one but by blocks of several characters).
Finally, cryptanalysis, for its part, consists of all the techniques and methods used to recover a clear text from an encrypted text. It is composed of decryption, operation by which from an encrypted message one finds the original message thanks to the encryption algorithm and the key, and of decryption, operation by which from an encrypted message one finds the original message, but without knowing the key or the decryption algorithm.
To understand the modern applications of cryptography, it must be stated that several great types of cryptography exist: symmetric cryptography, asymmetric cryptography and hybrid cryptography.
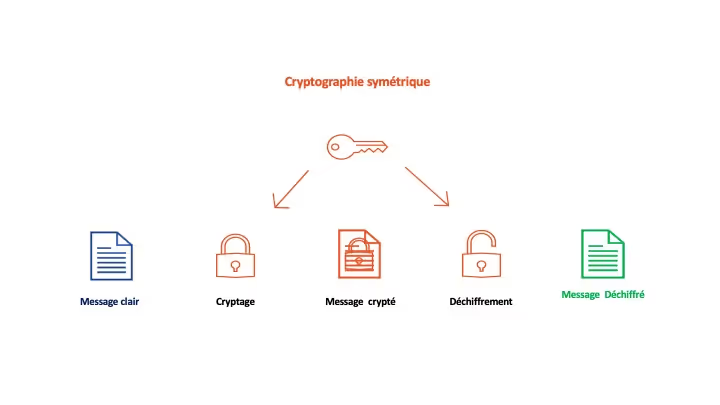
A cryptographic system is said to be symmetric if the key used for encryption is also the one used for decryption. In such a system, the correspondents agree in advance on a key before starting their message exchanges. Although it is simpler to implement than asymmetric cryptography, this system requires that the key be communicated and kept confidential by the correspondents. This is an important drawback because this key must be changed regularly to resist attacks from cryptanalysts. Moreover, the greater the number of correspondents, the greater the risk of losing the confidentiality of the key.
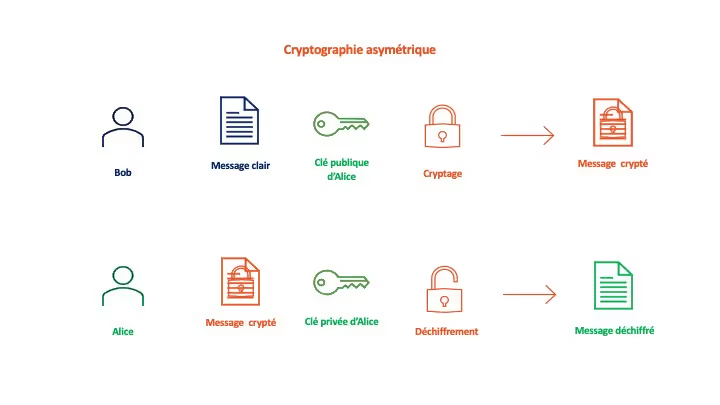
A cryptographic system is said to be asymmetric (or “public key”) if the key used for encryption is different from the one used for decryption. The correspondents each have a key that they keep secret and a public key that they communicate to everyone. To send a message, it is encrypted using the recipient’s public key. The recipient will use their secret key to decrypt it. In addition to its high level of security, the main advantage of asymmetric cryptography lies in the possibility of distributing the public key on a large scale. However, the encryption of information is much slower and requires more computer resources.
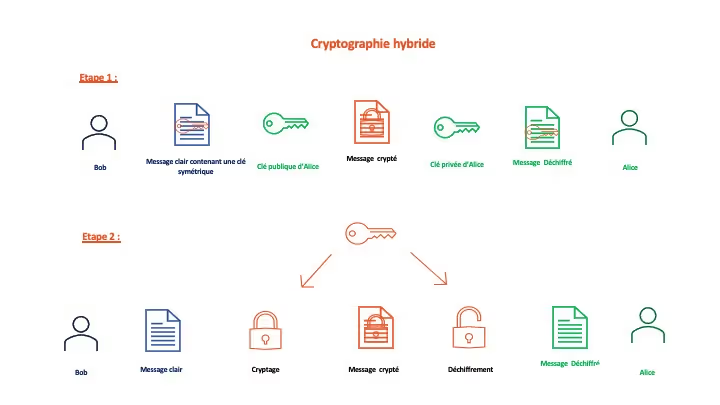
In order to overcome the disadvantages of asymmetric (cumbersome and complex) and symmetric encryption methods (risk of key communication), a hybrid encryption method has been developed: the sender determines a decryption key and uses an asymmetric encryption algorithm to encrypt it. Once the key is securely communicated to the recipient, the parties communicate using a symmetric encryption system
The first and historical utility of cryptology is to guarantee the preservation of the confidentiality of an information. The invention of the microprocessor in 1971 allowed cryptology to evolve and become more complex thanks to the computing power of computers.
Indeed, several symmetric and asymmetric encryption algorithms were developed and used:<
ul>
The RSA (Rivest, Shamir and Adleman, its creators) algorithm in 1977
The DES (Data Encryption Standard) algorithm in 1977 as well
The AES (Advanced Encryption Standard) algorithm in 2000
The triple DES algorithm in 2000
The Twofish and Blowfish algorithms, which were dated in 2000
In 1997, the U.S. National Institute of Standards and Technology (NIST) held a contest to determine which algorithm would be the encryption standard. The AES algorithm won this contest. It is a symmetric encryption algorithm and can generate encryption keys up to 256 bits in length.
Encryption is used in a variety of situations that require security measures to be implemented that ensure the confidentiality of an information. Article 32 of GDPR and the principle of privacy by design require data controllers to assess the need for the implementation of technical and organizational security measures prior to the operational start of a personal data processing. This assessment is done:
GDPR Art.32 (§1) “Taking into account the state of the art, the costs of implementation and the nature, scope, context and purposes of the processing as well as the risks“and
GDPR Art.32 (§2)taking into account “in particular the risks involved in the processing, resulting in particular from the destruction, loss, alteration, unauthorized disclosure of personal data transmitted, stored or otherwise processed, or unauthorized access to such data, whether accidental or unlawful.”
Indeed, encryption is explicitly mentioned in Article 32 (§1a) of GDPR as a security measure to be considered in order to ensure a level of security appropriate to the risk to data subjects.
Similarly, data encryption is explicitly recommended by the Commission Nationale de l’Informatique et des Libertés (CNIL), the Agence Nationale de la Sécurité des Systèmes d’Information (ANSSI) and the European Data Protection Board (EDPB) in multiple situations such as the use of secure messaging in the context of sensitive data transfers, encryption of data when it is transferred outside of the European Union, or encryption of personal data backups.
However, there is no legal obligation for data controllers to implement encryption measures in a direct and systematic way. Nevertheless, the CNIL has sanctioned two doctors for failure to comply with the data security obligation because they had not encrypted health data in a database belonging to them.
In order to be able to determine when and if it is appropriate to encrypt personal data, the data controller must consider the interest and the effective applicability of this measure to the personal data processing envisaged. Data encryption can only be used effectively when data is in transit or at rest. Indeed, once data is encrypted, it cannot be read (and therefore processed for the purposes for which it was collected) until it is decrypted. However, decryption increases the risk of loss of confidentiality, on the one hand because it implies the use of the decryption key, which presents a risk for one’s own confidentiality, and on the other hand because at rest, the data regains its original vulnerability.
This is why the EDPB considers that this measure alone is insufficient to guarantee a level of protection equivalent to that guaranteed by GDPR for data that would be transferred outside the European Union: if the recipient has to decrypt the data in order to process it, its confidentiality is no longer guaranteed and a third party can access it.
It should also be noted that today, the functions performed by cryptology have evolved.
In addition to the confidentiality of an exchange of information, it now guarantees:
The integrity of a message: the information cannot be modified by an unauthorized person.
The authenticity of a message: the information is attributed to its legitimate author.
Thanks to the so-called “hash” system, it is now possible to determine whether a message has been modified between the time it was sent by its sender and its reading by the recipient. A hash function makes it possible to associate a unique fingerprint, verifiable by all, with a message, file or directory. This fingerprint is often materialized by a long sequence of numbers and letters preceded by the name of the algorithm used (SHA2 or SHA256 for example). It varies according to the different components of the hashed element: size, number of characters, extension etc.
Thus, by comparing the two “hashes” produced when a document is sent and when it is received, the sender and the recipient can be sure of the integrity of the element transmitted.
However, it is also possible to use hashing techniques that involve the use of a secret key. This method modifies the fingerprint according to the key used and it is therefore possible to obtain two different hashes from the same document. The comparison of the two hashes can then only guarantee the integrity of the message if the sender and the recipient of the message use the same secret key to proceed with the hash.
Hashing is also used for password verification. Storing user passwords in the clear in a database is very risky if the file is compromised. Instead of storing the password, it is therefore more common to store a hashed version of the password. To authenticate a user, the password provided by the user is hashed and compared with the stored hash value.
The mechanism of the cryptographic signature makes it possible to ensure the authenticity of its origin. Thus, by signing a document with his private key, a person can allow any third party to verify his identity thanks to a public key, known by all. The electronic signature has become an essential tool during the health crisis because of the democratization of telecommuting. According to Article 1366 of the French Civil Code, it has the same probative force as a handwritten signature. However, it should not be confused with the digital signature (drawn by the signatory, or inserted by an image), which does not have the same probative force, because it does not allow to identify in a sure and integrated way the author of this signature.
The electronic signature is governed by the EIDAS regulation, which distinguishes three types of security levels for electronic signatures:
1. Standard
This is the digital signature as defined above. It can be used as prima facie evidence in writing but does not guarantee the integrity of the signed data or the identity of the signatory.
2. Advanced
This is the most commonly used signature for businesses. A private key accessible only to the signer allows
In order to be valid, this requires the acquisition of an electronic signature certificate that meets the requirements of the EIDAS regulation.
3. Qualified
This is the most technically and legally robust electronic signature. This type of signature requires that the identity of the signatory be validated upstream by an authorized third party (certification authority or electronic qualification service provider), and that a specific signature device (physical token) be issued to the signatory. It is this signature process which, according to the civil code, is the equivalent of the handwritten signature.
– Oscar Lourdin
GDPR and Compliance
Outsourced DPO & Representation
Training & Support




To give you 100% control over the design, together with Webflow project, you also get the Figma file. After the purchase, simply send us an email to and we will e happy to forward you the Figma file.
Yes, we know... it's easy to say it, but that's the fact. We did put a lot of thought into the template. Trend Trail was designed by an award-winning designer. Layouts you will find in our template are custom made to fit the industry after carefully made research.
We used our best practices to make sure your new website loads fast. All of the images are compressed to have as little size as possible. Whenever possible we used vector formats - the format made for the web.
Grained is optimized to offer a frictionless experience on every screen. No matter how you combine our sections, they will look good on desktop, tablet, and phone.
Both complex and simple animations are an inseparable element of modern website. We created our animations in a way that can be easily reused, even by Webflow beginners.
Our template is modular, meaning you can combine different sections as well as single elements, like buttons, images, etc. with each other without losing on consistency of the design. Long story short, different elements will always look good together.
On top of being modular, Grained was created using the best Webflow techniques, like: global Color Swatches, reusable classes, symbols and more.
Grained includes a blog, carrers and projects collections that are made on the powerful Webflow CMS. This will let you add new content extremely easily.
Grained Template comes with eCommerce set up, so you can start selling your services straight away.
To give you 100% control over the design, together with Webflow project, you also get the Figma file.