What Does the GDPR Mean for Cyber Security?
-min.avif)
-min.avif)
As cyber threats grow more sophisticated, simply updating privacy policies or managing cookie consent is no longer enough. Instead, businesses must embed cyber security into every layer of data management. This is the core principle of GDPR data security requirements.
Besides being a compliance requirement, it represents a fundamental shift in how we handle and protect data. Let’s explore the role of GDPR cyber security and how it impacts businesses.
GDPR data security requirements have become essential for maintaining consumer trust and avoiding severe penalties. This section will delve into the specifics of the GDPR and its implications for cybersecurity.
The General Data Protection Regulation (GDPR) is a landmark data privacy law introduced by the European Union (EU). It harmonises data protection rules across member states and enhances the rights of individuals.
It came into effect on May 25, 2018, replacing the 1995 EU Data Protection Directive. The GDPR cyber security applies to any business or organisation processing EU residents' personal data, regardless of the location. This makes it one of the most far-reaching privacy regulations globally.
From stronger encryption and access controls to proactive threat detection and breach response, GDPR data security requirements are extensive. When businesses fully comply with these requirements, they can address threats before they become full-blown crises.
The GDPR mandates organisations to implement "appropriate technical and organisational measures" to shield personal data from unauthorised access, theft, and breaches. This includes practices like access controls, encryption, and regular security audits for confidentiality, integrity, and availability of data.
The regulation also introduces strict data breach notification rules. Under Article 33 of the GDPR, the data controllers need to report incidents to the Data Protection Authority (DPA) within 72 hours. This helps ensure a proactive approach to addressing cybersecurity breaches.
GDPR cyber security compliance forms the backbone of an organisation’s data protection strategy.. Let’s break down three critical areas where the GDPR intersects with cyber security.
Building privacy into your systems is essential under GDPR network security, which mandates privacy by design and privacy by default.
GDPR security controls should be tailored to an organisation's size, data type, and associated risks. Here are some key practices to follow:
No matter how robust your defences are, breaches can still happen. The GDPR incident response requires organisations to not only prevent breaches but also have a solid plan for responding when they occur. To meet this requirement, the organisations should:
In case a breach occurs, here’s what IT teams should do to comply with GDPR incident response:
GDPR cyber security is not just a technical consideration but a legal and business necessity. Let’s explore how the GDPR aligns with existing frameworks, the risks of non-compliance, and how it compares with other regulations.
The GDPR complements various established cyber security frameworks. Here’s how it creates a robust foundation for protecting personal data:
Failing to comply with the GDPR can lead to certain repercussions:
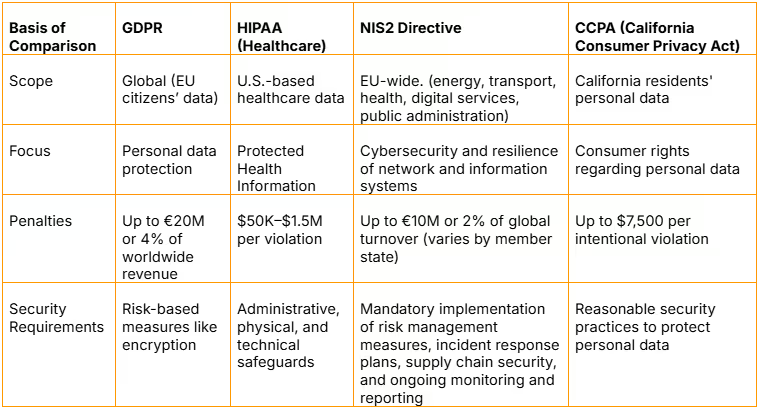
Let’s compare GDPR vs CCPA and other major regulations like HIPAA or PCI DSS
What is GDPR compliance? Achieving GDPR compliance requires a proactive approach to cybersecurity and data protection. Here are the key best practices:
Use multi-factor authentication (MFA) and role-based access control (RBAC) to grant access based on job roles to sensitive data. This strengthens both security and regulatory compliance.
Conducting regular audits helps identify vulnerabilities and ensure that security measures are effective. It keeps you ahead of evolving cyber threats while ensuring adherence to cybersecurity and data protection standards.
Simulate cyberattacks to test defences and identify weaknesses. This aligns with the GDPR’s requirement for robust technical measures.
Providing GDPR-focused cybersecurity training helps employees recognise threats such as phishing and adopt best practices. It reduces the risk of data breaches. GDPR training also helps employees better understand security protocols.
Create an incident response plan and data breach response plan to detect and contain breaches as early as possible.. It ensures compliance with GDPR, such as the 72-hour breach notification requirement..
Small cyber security mistakes can result in significant GDPR violations. Key pitfalls include:
Simple passwords and a lack of multi-factor authentication allow unauthorised access. Role-based access is essential to protect sensitive data.
Unencrypted sensitive information is vulnerable. The GDPR mandates encryption for data protection, especially during transmission and storage.
As per GDPR security requirements, breaches must be reported within 72 hours.. Thus, having a breach detection and response plan is crucial for compliance.
Outsourcing security without proper oversight can create vulnerabilities. Organisations must regularly assess third-party security practices to ensure GDPR vulnerability compliance.
As technology evolves, the GDPR remains crucial in how organisations manage personal data, especially with AI and cloud computing.
AI improves cyber security but poses the following GDPR challenges:
Cloud computing is essential but complicates GDPR vulnerability compliance in the following ways:
Don't let GDPR compliance overwhelm you! With top-notch security audit services, you can ensure your organisation is meeting regulatory requirements while building a robust cyber security posture. Leverage services from DPO Consulting to help you navigate the complexities of the GDPR. From implementing strong GDPR security controls to conducting thorough risk assessments, we take care of your compliance needs.
DPO Consulting is a leading GDPR compliance service provider. With tailored strategies, we help you with DSAR compliance, streamline processes, and maintain strong data subject privacy practices. By partnering with specialists, businesses can benefit from the latest industry insights, reduce compliance risks, and improve their overall DSAR process efficiency.
DPO consulting encourages organizations to regularly review their DSAR policy and incorporate the changes as required. This continuous improvement mindset is crucial for adapting to evolving regulations and ensuring that the rights of data subjects are consistently upheld.
Yes, a DPO is mandatory for public authorities and for organisations that process large-scale monitoring of individuals or large-scale special categories of personal data.
You must respond to data subject requests within a month, providing access, rectification, erasure, or restriction of processing as requested, unless an extension of up to two additional months is justified due to complexity or number of requests.
GDPR applies to all personal data, including special categories of data such as health information, genetic and biometric data, racial or ethnic origin, and political or religious beliefs.
DPIAs should be conducted whenever processing operations are likely to result in a high risk to individuals, such as large-scale processing, systematic monitoring, or processing of special categories of personal data.
The GDPR grants individuals rights such as access, rectification, erasure (right to be forgotten), data portability, and objection to processing.
Investing in GDPR compliance efforts can weigh heavily on large corporations as well as smaller to medium-sized enterprises (SMEs). Turning to an external resource or support can relieve the burden of an internal audit on businesses across the board and alleviate the strain on company finances, technological capabilities, and expertise.
External auditors and expert partners like DPO Consulting are well-positioned to help organizations effectively tackle the complex nature of GDPR audits. These trained professionals act as an extension of your team, helping to streamline audit processes, identify areas of improvement, implement necessary changes, and secure compliance with GDPR.
Entrusting the right partner provides the advantage of impartiality and adherence to industry standards and unlocks a wealth of resources such as industry-specific insights, resulting in unbiased assessments and compliance success. Working with DPO Consulting translates to valuable time saved and takes away the burden from in-house staff, while considerably reducing company costs.
GDPR and Compliance
Outsourced DPO & Representation
Training & Support




To give you 100% control over the design, together with Webflow project, you also get the Figma file. After the purchase, simply send us an email to and we will e happy to forward you the Figma file.
Yes, we know... it's easy to say it, but that's the fact. We did put a lot of thought into the template. Trend Trail was designed by an award-winning designer. Layouts you will find in our template are custom made to fit the industry after carefully made research.
We used our best practices to make sure your new website loads fast. All of the images are compressed to have as little size as possible. Whenever possible we used vector formats - the format made for the web.
Grained is optimized to offer a frictionless experience on every screen. No matter how you combine our sections, they will look good on desktop, tablet, and phone.
Both complex and simple animations are an inseparable element of modern website. We created our animations in a way that can be easily reused, even by Webflow beginners.
Our template is modular, meaning you can combine different sections as well as single elements, like buttons, images, etc. with each other without losing on consistency of the design. Long story short, different elements will always look good together.
On top of being modular, Grained was created using the best Webflow techniques, like: global Color Swatches, reusable classes, symbols and more.
Grained includes a blog, carrers and projects collections that are made on the powerful Webflow CMS. This will let you add new content extremely easily.
Grained Template comes with eCommerce set up, so you can start selling your services straight away.
To give you 100% control over the design, together with Webflow project, you also get the Figma file.