Comprehensive Guide to Cybersecurity Risk Assessment


The threat of cyberattacks is ever-present, posing significant risks to businesses of all sizes. As a result, ensuring strong cybersecurity practices is no longer optional but essential. One of the most crucial elements in securing an organization's data and digital assets is conducting a thorough cybersecurity risk assessment. This guide will walk you through the various stages of a cybersecurity risk assessment, why it’s important, and best practices for ensuring your business remains protected.
Cyber risk refers to the potential for harm to an organization's information systems, data, or operations due to a cybersecurity threat. These threats can come from various sources, such as hackers, malware, insider threats, or system vulnerabilities. Cyber risk is the likelihood of these threats materializing and causing damage to the organization, ranging from financial losses to reputational damage.
As businesses increasingly rely on technology to operate, cyber risk becomes an unavoidable part of the organizational landscape. In fact, as per Official Statistics published of Cyber security breaches survey 2024 published by UK govt, 50% of UK businesses, experienced some form of cyber attack in 2023. Thus, understanding the nature of cyber risks and taking steps to mitigate them is critical to maintaining business continuity and safeguarding sensitive data.
A cybersecurity risk assessment is a systematic process used to identify, evaluate, and prioritize risks related to an organization’s information technology systems and data. This process helps to determine which areas of the organization are most vulnerable to cyberattacks and what measures should be implemented to reduce the likelihood or impact of a breach.
Organizations often have a cybersecurity governance process that involves several stages, such as identifying critical assets, assessing vulnerabilities, evaluating the impact of potential threats, and determining appropriate mitigation strategies. By conducting regular risk assessments, organizations can better understand their cybersecurity posture and ensure that appropriate defenses are in place to protect against emerging threats.
Cybersecurity risk assessments are vital for several reasons:
To conduct an effective cybersecurity risk assessment, follow these essential steps:
The first step in the cybersecurity risk assessment process is to identify the critical assets and resources that need protection. This includes data, systems, networks, hardware, and personnel. Once these assets are identified, it is important to understand their role within the organization and how a compromise could affect business operations.
The next step is to identify potential threats to your organization’s cybersecurity. These could include external threats, such as cybercriminals and hackers, as well as internal threats like disgruntled employees or accidental data breaches. Evaluate each threat based on its likelihood and potential impact on your critical assets.
Once threats are identified, the next step is to assess the vulnerabilities that could be exploited by these threats. Vulnerabilities may include outdated software, unpatched systems, weak passwords, or inadequate data encryption. The more vulnerable an asset is, the higher the risk it poses to the organization.
Evaluate the potential impact of a cybersecurity breach or threat on each of your critical assets. This includes considering financial losses, legal implications, reputational damage, and operational disruptions. Understanding the potential consequences helps to prioritize which risks to address first.
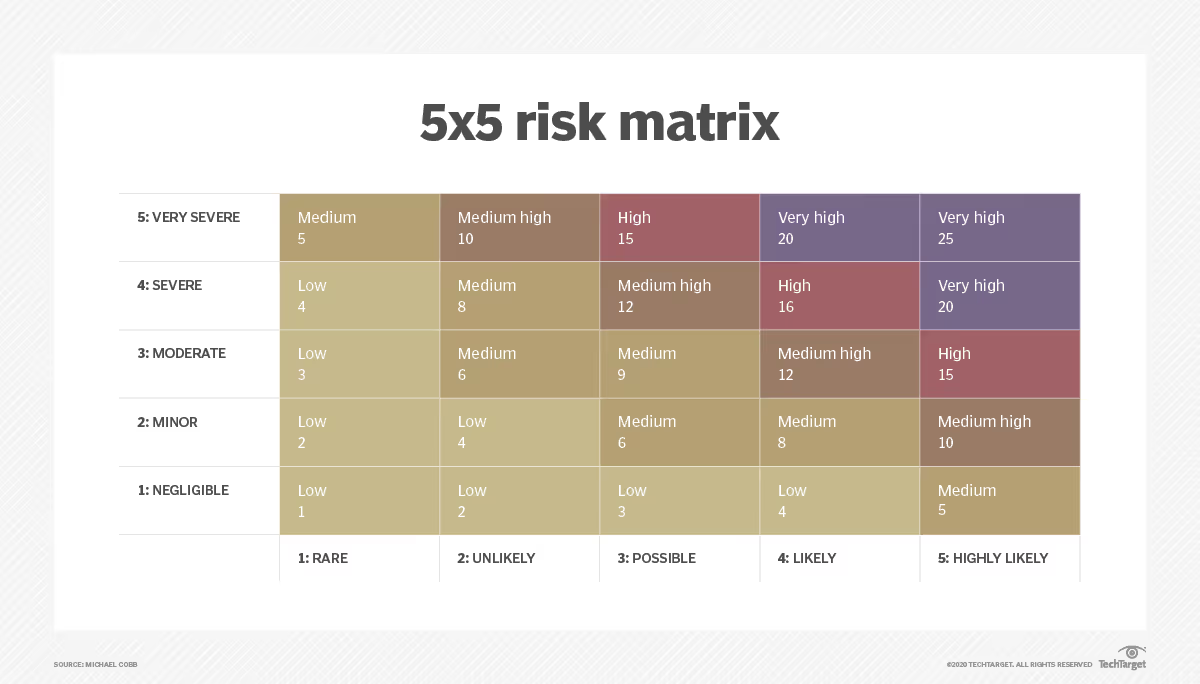
Source: TechTarget
For each identified risk, assess both the likelihood of the threat occurring and the potential impact it could have on the organization. This helps in evaluating which risks are most critical and need immediate attention.
Based on the risk assessment, develop a cybersecurity risk assessment plan that includes strategies to mitigate each identified risk. This might involve implementing new security controls, improving employee training, or investing in advanced cybersecurity tools.
Cybersecurity is a dynamic field, and new threats emerge regularly. Regular monitoring and periodic reassessments are crucial for ensuring your cybersecurity measures remain effective. Make adjustments to your security plan as necessary to respond to changing threats and vulnerabilities.
Selecting the right framework and methodology is crucial when conducting a cybersecurity risk assessment. The framework will guide you in evaluating the risks in a structured manner, while the methodology will provide the process for managing them effectively.
There are several risk assessment frameworks available, each offering unique approaches to cybersecurity risk management. Some of the most widely used frameworks include:
Methodologies for conducting cybersecurity risk assessments vary depending on the organization's needs and the chosen framework. The most common methodologies include:
Conducting a cybersecurity risk assessment is not without its challenges. Some common obstacles include:
To overcome these challenges and conduct an effective cybersecurity risk assessment, follow these best practices:
Cybersecurity is not a one-time task but an ongoing process. The threat landscape is constantly changing, and organizations must continuously assess and update their security measures to stay protected. Ongoing risk assessments help organizations detect new vulnerabilities and respond to emerging threats before they can cause damage.
At DPO Consulting, we understand the importance of cybersecurity in this digital environment. As your trusted GDPR compliance partner, we help organizations conduct thorough cybersecurity risk assessments and provide security audit services that align with global standards. Our approach is comprehensive, ensuring that all vulnerabilities are identified and mitigated effectively. From identifying critical assets to developing a cybersecurity risk assessment plan, we guide you through every step of the process.
Start by defining your objectives and identifying critical assets, such as sensitive data, networks, and essential systems. Form a cross-functional team from IT, security, and compliance. Choose a framework, like NIST or ISO 27001, that aligns with your goals. Collect relevant documentation—such as security policies, network diagrams, and any past assessments—to provide context and streamline the cyber security risk assessment process.
According to NIST, a security risk assessment identifies and evaluates threats, vulnerabilities, and the impact of potential security incidents. It involves a structured process for understanding risks to IT systems and data, helping organizations make informed decisions to protect critical assets.
Cybersecurity risk is typically measured by evaluating the likelihood of a threat exploiting a vulnerability and the potential impact of a successful attack. Organizations often use qualitative or quantitative methods, considering factors like financial loss, operational disruption, and reputational harm.
Key steps include identifying critical assets, assessing potential threats and vulnerabilities, evaluating the impact of risks, determining the likelihood of occurrence, and developing strategies to mitigate identified risks. Finally, monitor and review assessments regularly.
Organizations should conduct cybersecurity risk assessments at least annually, with additional assessments after significant system changes or in response to emerging threats.
Common challenges include limited resources, evolving threats, complex IT environments, and meeting regulatory compliance requirements. Overcoming these challenges requires planning, collaboration, and sometimes external expertise.
Small businesses can conduct effective risk assessments by focusing on their most critical assets, leveraging cost-effective cybersecurity tools, and using simplified frameworks. Outsourcing to specialists for periodic reviews can also provide insights without requiring extensive in-house resources.
Investing in GDPR compliance efforts can weigh heavily on large corporations as well as smaller to medium-sized enterprises (SMEs). Turning to an external resource or support can relieve the burden of an internal audit on businesses across the board and alleviate the strain on company finances, technological capabilities, and expertise.
External auditors and expert partners like DPO Consulting are well-positioned to help organizations effectively tackle the complex nature of GDPR audits. These trained professionals act as an extension of your team, helping to streamline audit processes, identify areas of improvement, implement necessary changes, and secure compliance with GDPR.
Entrusting the right partner provides the advantage of impartiality and adherence to industry standards and unlocks a wealth of resources such as industry-specific insights, resulting in unbiased assessments and compliance success. Working with DPO Consulting translates to valuable time saved and takes away the burden from in-house staff, while considerably reducing company costs.
GDPR and Compliance
Outsourced DPO & Representation
Training & Support




To give you 100% control over the design, together with Webflow project, you also get the Figma file. After the purchase, simply send us an email to and we will e happy to forward you the Figma file.
Yes, we know... it's easy to say it, but that's the fact. We did put a lot of thought into the template. Trend Trail was designed by an award-winning designer. Layouts you will find in our template are custom made to fit the industry after carefully made research.
We used our best practices to make sure your new website loads fast. All of the images are compressed to have as little size as possible. Whenever possible we used vector formats - the format made for the web.
Grained is optimized to offer a frictionless experience on every screen. No matter how you combine our sections, they will look good on desktop, tablet, and phone.
Both complex and simple animations are an inseparable element of modern website. We created our animations in a way that can be easily reused, even by Webflow beginners.
Our template is modular, meaning you can combine different sections as well as single elements, like buttons, images, etc. with each other without losing on consistency of the design. Long story short, different elements will always look good together.
On top of being modular, Grained was created using the best Webflow techniques, like: global Color Swatches, reusable classes, symbols and more.
Grained includes a blog, carrers and projects collections that are made on the powerful Webflow CMS. This will let you add new content extremely easily.
Grained Template comes with eCommerce set up, so you can start selling your services straight away.
To give you 100% control over the design, together with Webflow project, you also get the Figma file.